Strategies for Eliminating VM Sprawl: A Practical Approach
Unmanaged growth of virtual machines, known as VM sprawl, leads to inefficient resource utilization, increased costs, and significant administrative difficulties, necessitating proactive prevention.
Learn how to identify, manage, and stop VM sprawl with this step-by-step guide.
VM Sprawl:
When VMs are created without governance and left running beyond their intended lifespan, VM sprawl develops. This unnecessary resource consumption results in,
Resource under utilization: Inactive virtual machines consume memory, CPU, and storage resources without providing corresponding value.
Cost surge: Unnecessary VMs drive up costs through licensing, hardware, and energy consumption. This not only increases direct expenses but also diverts budget away from innovation and strategic IT projects.
Security risks: Unmanaged VMs pose significant security risks due to lack of patching and monitoring. VM sprawl complicates security policy enforcement, vulnerability tracking, and patch deployment, increasing the likelihood of compliance breaches and data leaks.
Strategies for mitigating virtual machine sprawl
1. Do an inventory check:
Initiate the process by establishing a complete inventory of all virtual machines within your environment. Employ tools or scripts to compile detailed information, including:
- Time of creation
- Owner / Requestioner
- Utilization metrics (CPU, memory, storage, network)
- Intended function and operational state (Active, Inactive, or ceased)
- Base operating system and deployed software packages
- Security configurations (patch levels, firewall rules)
Conducting this audit allows you to pinpoint unnecessary or underutilized VMs and security risks. For a complete understanding, utilize automated tools to map VM and application dependencies.
2. Terminate unused VMs:
Review your inventory and remove VMs you don’t need. This involves,
- Idle VMs: Devices demonstrating sustained low or zero resource utilization.
- Abandoned VMs: VMs with no owner and no work
- Duplicate VMs: Duplicate or non-essential backup datasets
Always back up VM data before deletion, particularly if there’s a possibility of needing it later.
3. Deploy governance mechanisms:
Set up policies to manage how VMs are made and used,
- Obtain permission: Implement a mandatory authorization process for virtual machine provisioning to guarantee alignment with organizational requirements and mitigate the risk of unauthorized deployments.
- Period of utilization: Establish a system for assigning predetermined expiration dates to transient virtual instances, with automated procedures for either their termination or a review assessment following the designated period
- Ownership allocation: Establish a protocol wherein each virtual machine is assigned a designated owner, who shall be held accountable for its maintenance, security, and subsequent decommissioning.
- Resource limits: Control resource usage by setting quotas for CPU, memory, and storage, ensuring individuals or departments use resources efficiently and avoid over provisioning.
- Automated workflow authorization: Make sure VM creation requires approval to ensure oversight and stop unauthorized VMs.
4. Utilize monitoring tools:
Utilize virtual machine monitoring solutions to monitor resource utilization, performance indicators, and security configurations. These solutions help discover,
- VMs that aren’t being used enough and might need to be optimized or combined.
- Hosts with too much demand, requiring load balancing or resource adjustments.
- Performance degradation and potential operational disruptions resulting from resource contention.
Receive alerts for unusual activity with monitoring tools, improving control. Set VM performance baselines for quick issue identification. Utilize predictive analytics to anticipate resource needs and proactively prevent sprawl.
5. Workload consolidation:
Reduce VM count and improve resource utilization by consolidating workloads from underutilized machines. Use resource utilization analysis to right-size VMs, providing necessary resources without excess.
6. Use automation for VM lifecycle management:
Automation tools make VM management easier by efficiently handling tasks from start to finish.
Auto deletion: Set VMs to automatically delete after a time limit or when they complete their tasks.
Categorizing: Label VMs using metadata to sort them by purpose, owner, or department, which helps with organization and management.
Infrastructure as Code(IaC): Use IaC to automatically set up, configure, and manage VMs, which reduces manual work and ensures consistency.
Configuration Management: Use configuration management tools to keep VMs in the right state, preventing changes and ensuring compliance.
7. Train teams:
Teach teams why VM governance matters and how sprawl hurts. Encourage these best practices:
- Optimizing workload distribution
- Asking for VMs only when required
- Matching VM size to needs
- Implementing security policy adherence
Implement targeted training programs and workshops on VM best practices and sprawl prevention. Enhance engagement by incorporating gamification to motivate teams to optimize VM usage and reduce sprawl.
8. Perform periodic audits and remediation
Proactively manage VM sprawl by conducting regular audits and scheduling periodic cleanups. Track key metrics and generate reports to optimize resource use and measure progress. Perform root cause analysis to prevent future sprawl.
Avoiding future VM sprawl
Stopping VM sprawl in the future is just as important as getting rid of the sprawl we have now.
Integrated management: Use central tools to see everything that VMs are doing across the entire system.
Pre-set workflows: Develop and institute well-defined procedural frameworks for virtual machine requisition, approval, and provisioning.
Resource planning: Keep an eye on infrastructure capacity to avoid wasting resources and make sure they’re there when you need them.
Documentation: Track all the details about VM creation, who owns them, and what they’re used for.
ManageEngine OpManager Plus: VM sprawl control and efficient VM monitoring
VM sprawl reduces the efficiency and performance of virtual infrastructure. By implementing proactive governance, audits, and automation, you can regain control of your VMware environment.
With robust virtualization management, OpManager Plus simplifies VM monitoring and eradicates sprawl. It automates VM discovery and mapping, providing a centralized dashboard for real-time insights into critical metrics like CPU, memory, and disk usage.

OpManager Plus automates the identification of underutilized VMs through proactive alerts, analytics, and reports, enabling rapid decommissioning. The solution not only controls but also prevents sprawl from returning.
The detailed capacity planning reports offered by the tool give valuable insights into resource trends, allowing you to forecast future needs and adjust allocations as well. This proactive approach, coupled with real-time alerts for performance anomalies, empowers IT teams to right-size VMs, consolidate resources, and decommission idle instances, ultimately preventing the uncontrolled proliferation of virtual machines and ensuring optimal resource allocation.
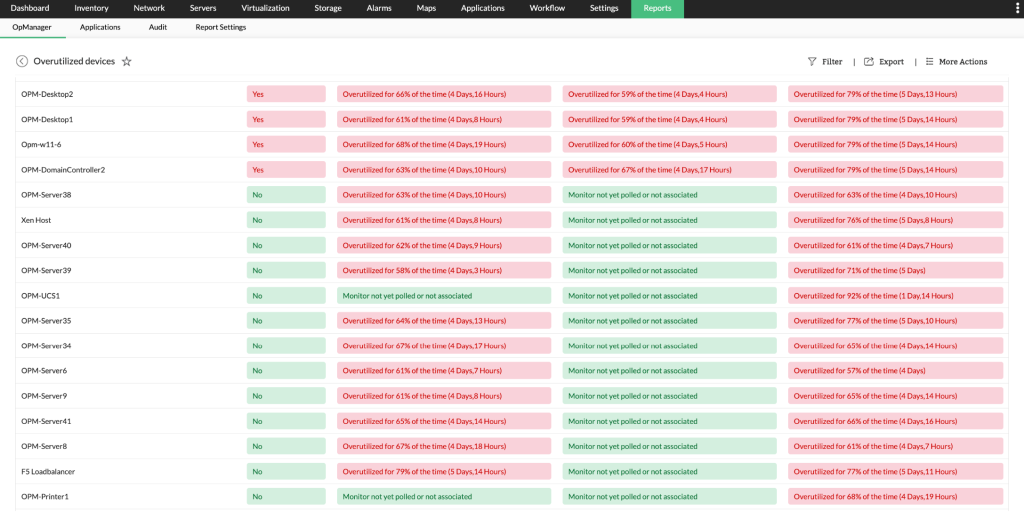
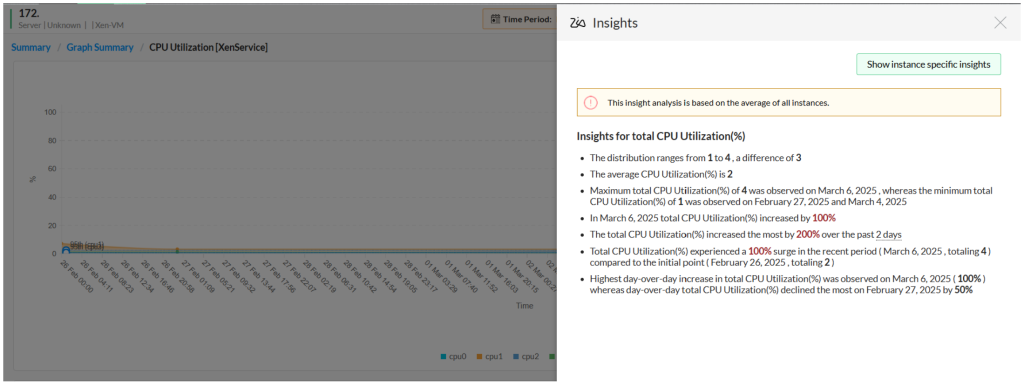
Adding to that, OpManager Plus props you with Zia, an AI-powered assistant. Zia Insights monitors your network 24/7, analyzes data to provide intelligent alerts and recommendations for action. If you need to pinpoint and remove VM sprawl , Zia insights can help you by identify overused VMs and flagging them, effectively reducing VM sprawl before it becomes a problem.
If you want to explore further the capabilities of OpManager Plus, check out the 30-day free trial and reduce VM sprawl while optimizing the potential of your VMware environment.


