How to Create/Modify NACLs and SGs in AWS
In AWS, Network Access Control Lists (NACLs) and Security Groups (SGs) are used to control traffic to and from your resource, much like a firewall. It’s also called Inbound and Outbound rules. But they serve slightly different purposes. NACLs operate at the subnet level and control traffic entering or leaving the subnet, while SGs operate at the instance level and control inbound and outbound traffic for instances.
Network Access Control Lists (NACLs) and Security Groups (SGs) play a pivotal role in controlling network traffic for your cloud resources. Let’s explore the process of creating and modifying NACLs and SGs, along with real-life examples.
Related: How to Configure User-Defined Routes in AWS
Creating NACL in AWS
Sign in to your AWS account and access the AWS Management Console.
Search “VPC” in the search bar.
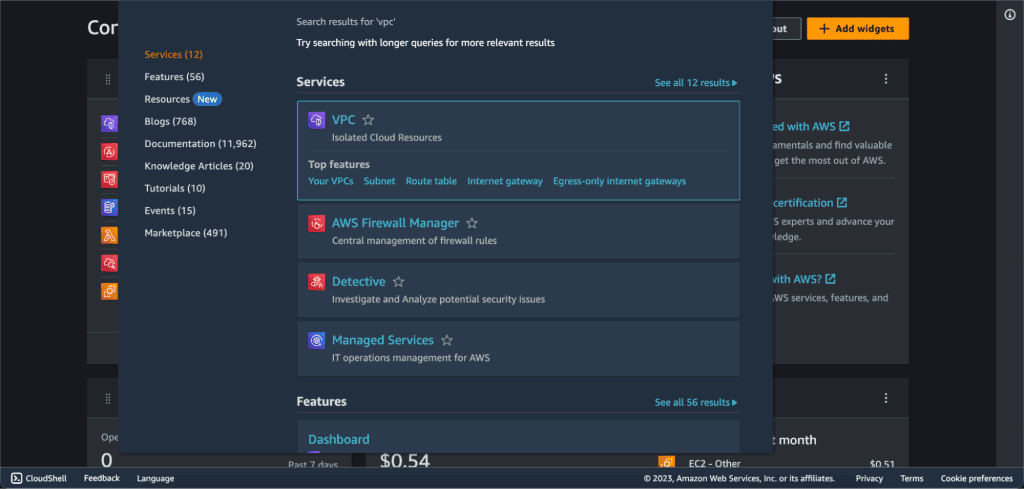
Navigate to the VPC Dashboard.
In the VPC Dashboard, choose “Network ACLs” from the left sidebar (It’s under Security).

Click the “Create Network ACL” button.

Provide a name for your NACL and choose the associated VPC.
Related: How to Create a VPC on AWS Step-by-Step
Click “Create” to create the new NACL.
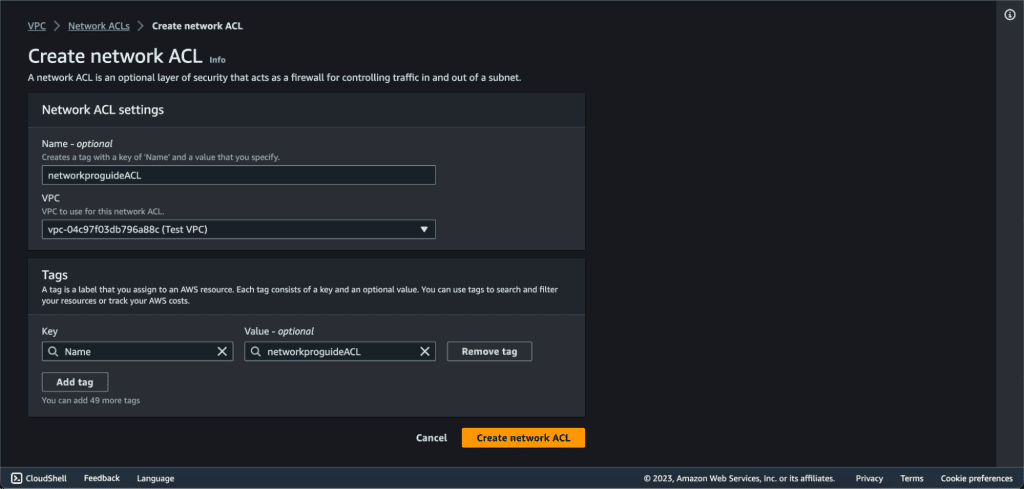
Example:
- Name: MyNACL
- VPC: Select your target VPC (It’s the VPC to which the NACL will be associated)
Modifying NACL in AWS
Modifying NACL rules allows you to customize traffic flow within your VPC’s subnets. Here’s how you can modify an existing NACL:
Select the NACL you want to modify.
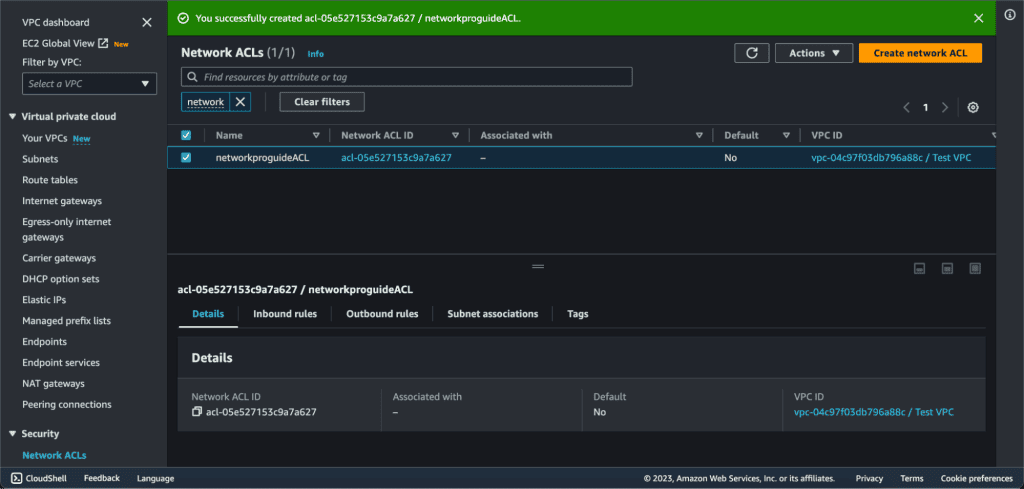
Go to the “Inbound Rules” tab to modify or delete inbound rules.
Click the “Edit inbound rules” button to make changes to the inbound rules.
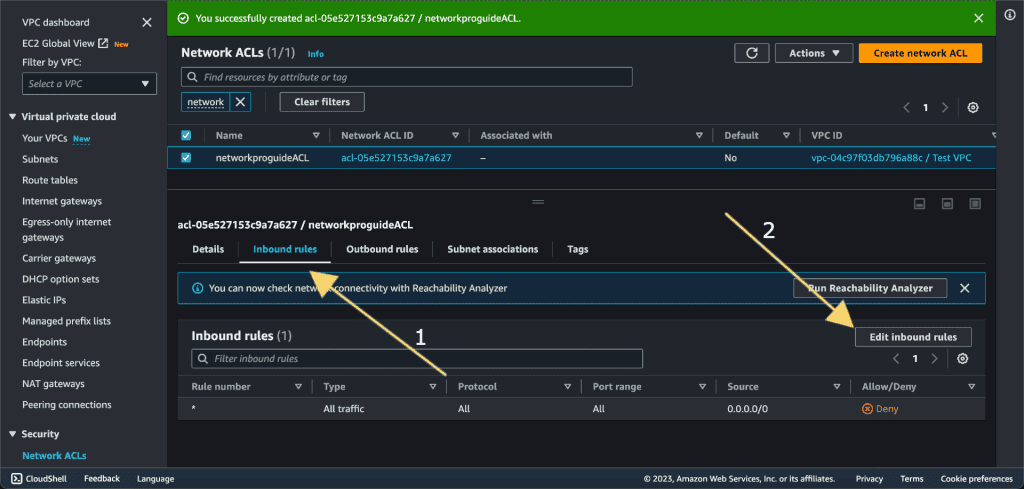
To add a new rule, click the “Add Rule” button.
For this example, we are now editing the rule which allows all HTTP traffic:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 80 (HTTP)
- Source: 0.0.0.0/0
- Allow/Deny: Allow
- Explanation: This rule allows incoming HTTP traffic from any destination, commonly used for web applications and websites. You can restrict the source to a specific range of IP addresses to enhance security.
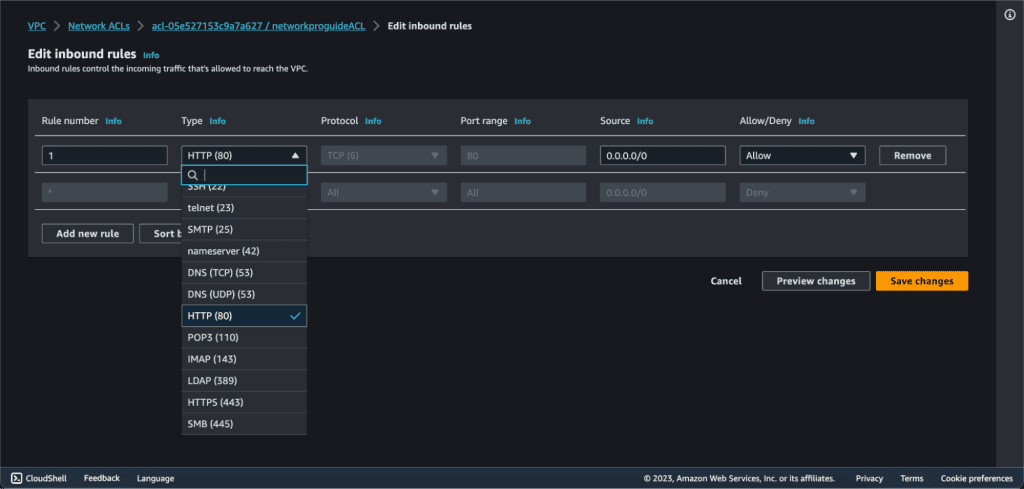
Now click on “Save Changes” then your inbound rules will be changed.
To change the outbound rules. Go to the “Outbound Rules” tab to modify or delete outbound rules
Click the “Edit outbound rules” button to change the rules.

To add a new rule, click the “Add Rule” button.
For this example, we are now editing the rule which allows all HTTPS traffic:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 443 (HTTP)
- Destination: 0.0.0.0/0
- Allow/Deny: Allow
- Explanation: This rule allows outgoing HTTPS traffic to any destination. You can restrict the source to a specific range of IP addresses to enhance security.
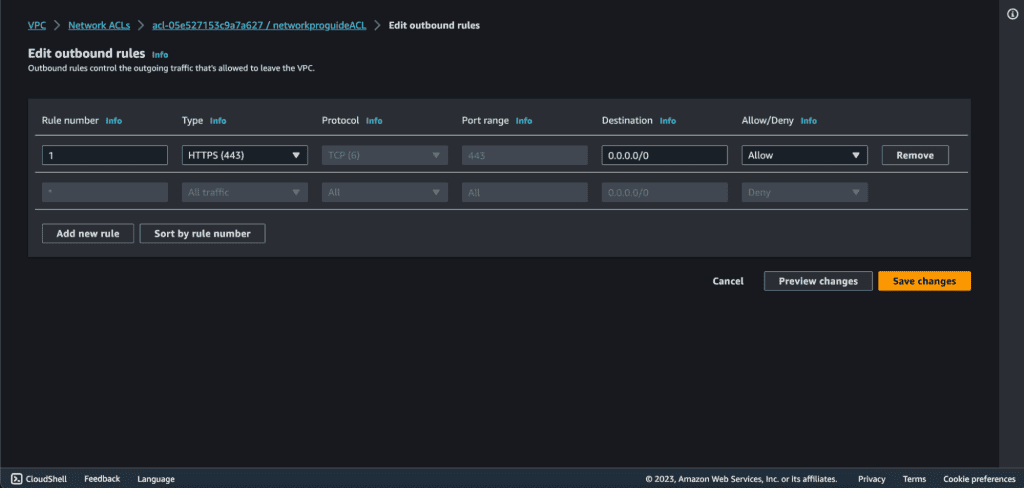
Click “Save rules” to apply the changes.
Creating SGs in AWS
In the AWS Management Console, Search “EC2.”
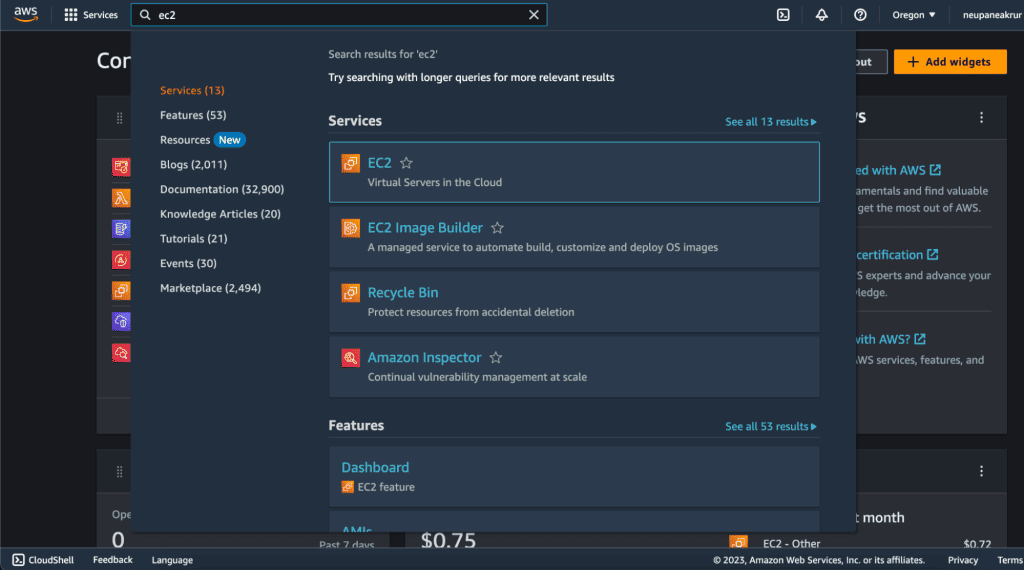
In the right sidebar go to the “Security Groups” inside the Network & Security tab.
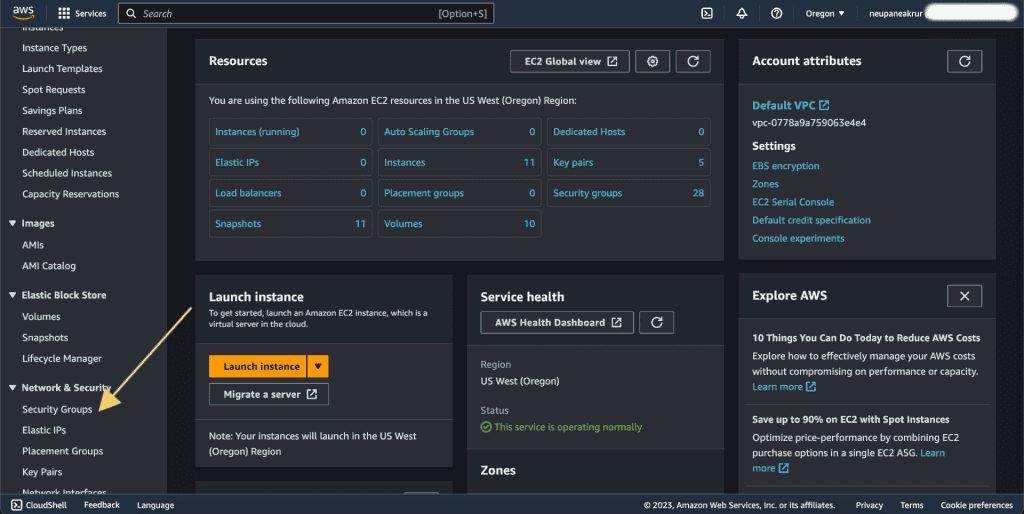
Click on a “Create Security Group.”
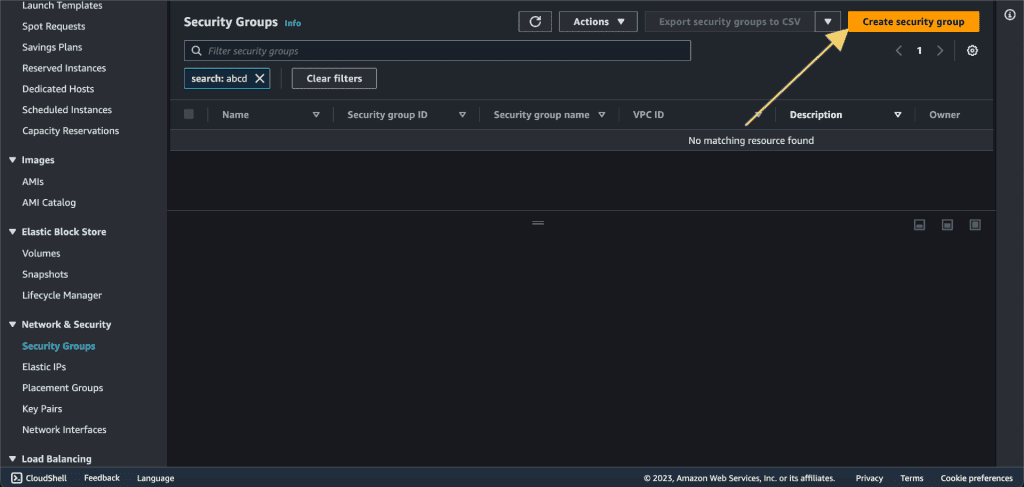
Give the name to the security group, write a description, and choose your desired VPC in which you are launching the EC2 instance.
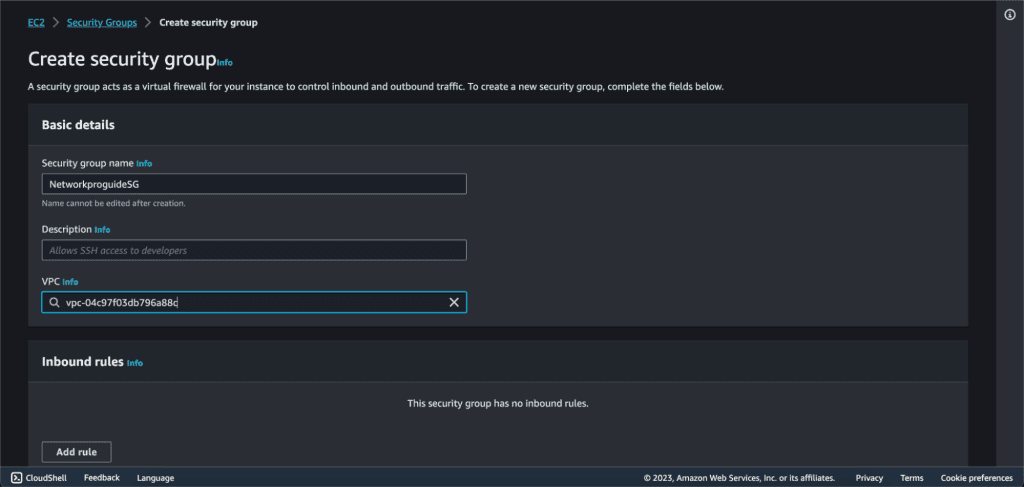
On the “Inbound Rules” tab, click on the “Add Rule” button.
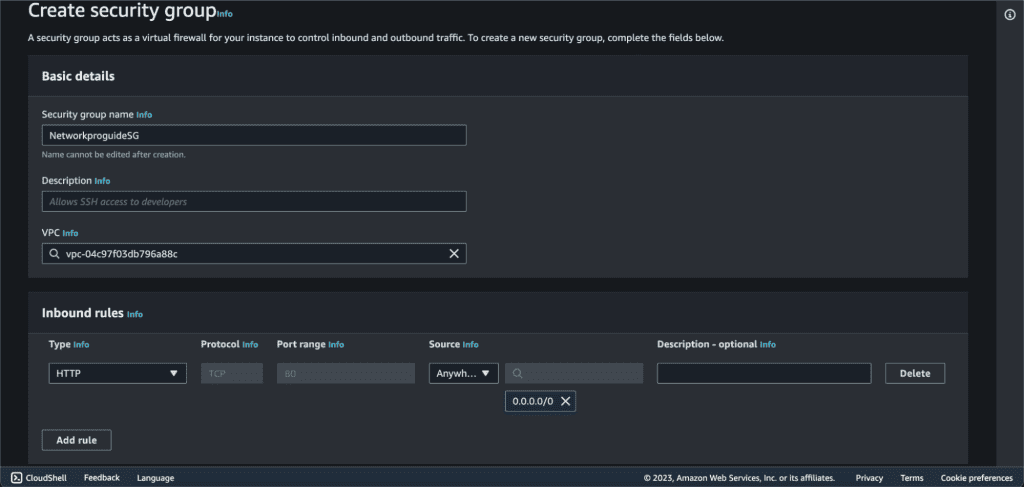
For this example, we are now editing the rule which allows all HTTP traffic:
- Type: HTTP
- Protocol: TCP
- Port Range: 80 (HTTP)
- Source: Anywhere-IPv4 (0.0.0.0/0)
- Explanation: This AWS Security Group rule allows unrestricted incoming HTTP traffic (port 80) from any IPv4 address to an EC2 instance.
On the “Outbound Rules” tab, click on the “Add Rule” button.

For this example, we are now editing the rule which allows network traffic to be sent from the instance:
- Type: All Traffic
- Protocol: All
- Port Range: All
- Destination: Custom (0.0.0.0/0)
- Explanation: This rule allows all types of network traffic to be sent from the instance to any destination IP address (0.0.0.0/0).
Now click on “Create security group”
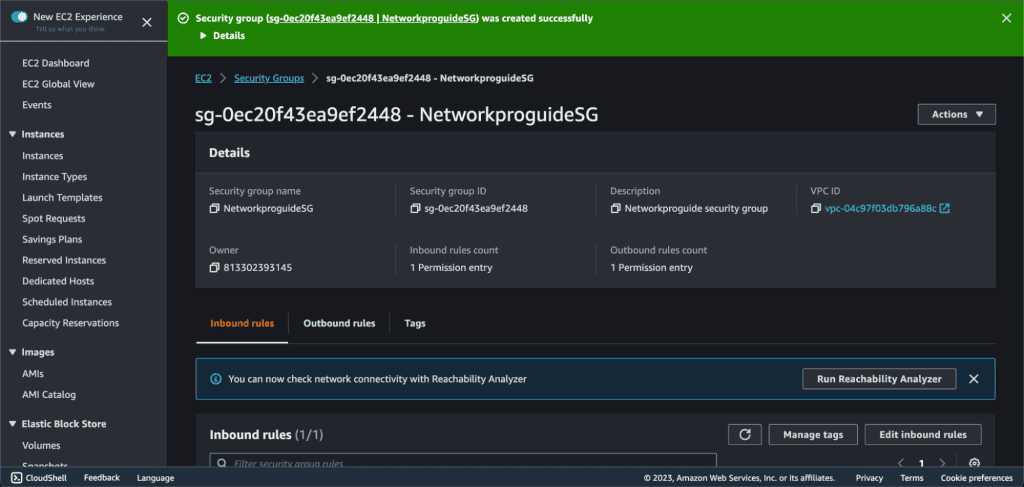
A new security group was created. Now you can launch an EC2 instance by attaching this security group.
Modifying the Security Group in AWS
Let’s modify the Security Group we just created.
Go to the “Security Groups” section, and select the Security Group that you have just created.
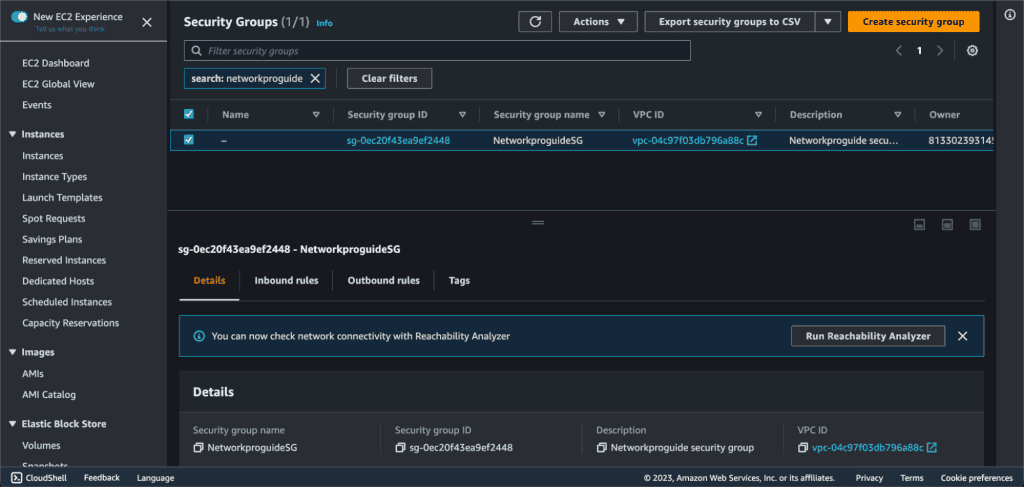
Go to the “Inbound Rules” tab, and click the “Edit inbound rules” button.

Click on “Add Rule” and select “SSH” in the type, “Anywhere IPv4” on the Source. Then click on “Save Rules”. It will allow SSH access in the EC2 instance. You can also delete the rule if you don’t want it.
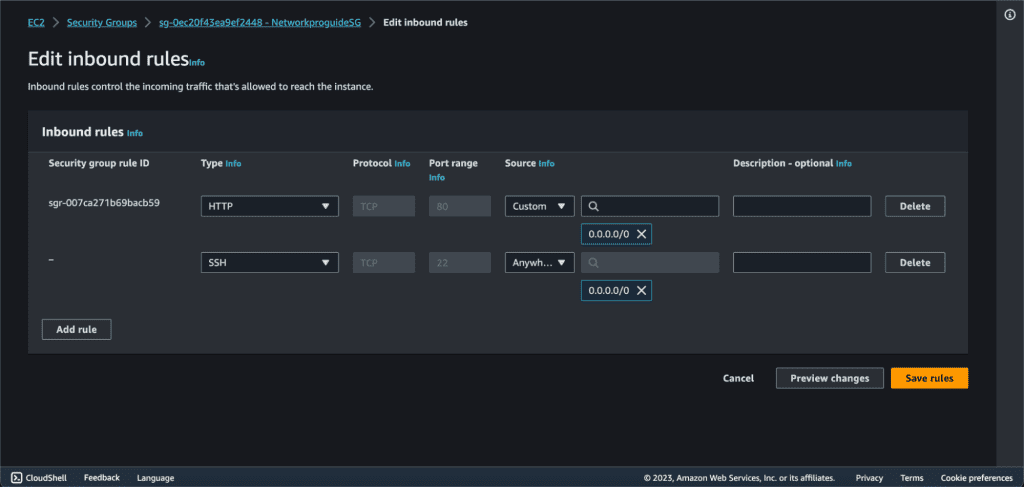
Now for the outbound rules, Go to the “Outbound Rules” tab, and click the “Edit outbound rules” button.
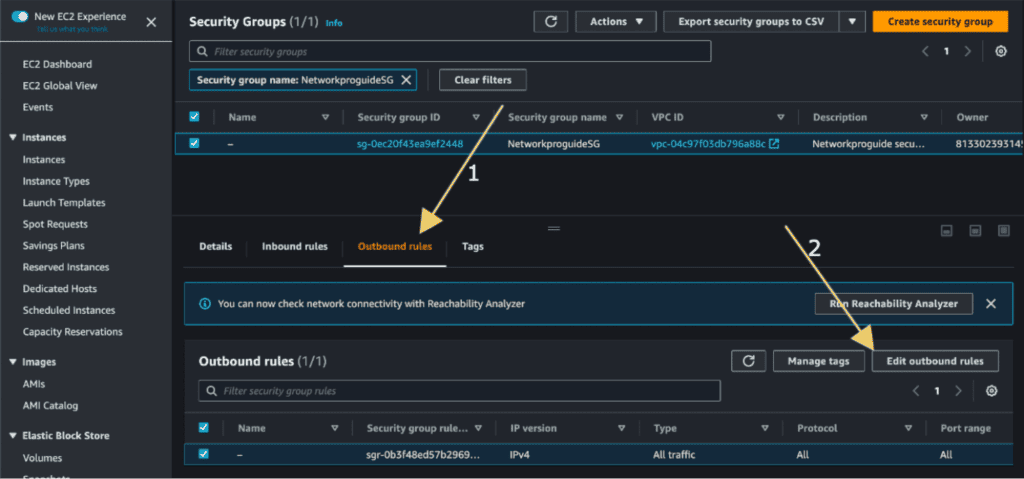
Click on “Add Rule” and select “HTTPS” in the type, “Anywhere IPv4” on the Source. Then click on “Save Rules”. It will allow HTTPS traffic to be sent from the EC2 instance. You can also delete the rule if you don’t want it.

Now you have successfully modified the security group.
Some commonly used NACL inbound and outbound rules, along with explanations of what they do:
Here are some commonly used Network Access Control List (NACL) inbound and outbound rules, along with explanations of what they do:
Inbound Rules:
SSH Access:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 22 (SSH)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: This rule allows incoming SSH traffic, often used for remote administration of instances. Limit the source IP range to trusted addresses to enhance security.
RDP Access:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 3389 (RDP)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: Similar to SSH, this rule enables Remote Desktop Protocol (RDP) traffic for Windows instances. Again, restrict the source IP range for better security.
Application-Specific Traffic:
- Rule: Rule number can be anything
- Protocol: TCP or UDP (based on application)
- Port Range: Application-specific port(s)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: Customize this rule for your application’s specific needs. It permits incoming traffic for a particular application, such as a database or API, from authorized sources.
ICMP (Ping) Requests:
- Rule: Rule number can be anything
- Protocol: ICMP
- Port Range: N/A (ICMP has no ports)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: This rule enables ICMP echo requests (ping), useful for network troubleshooting and monitoring. Specify allowed source IPs for controlled access.
VPN Traffic:
- Rule: Rule number can be anything
- Protocol: All (or specific protocols)
- Port Range: All (or specific ports)
- Source: IP addresses of VPN gateway or endpoints
- Allow/Deny: Allow
- Explanation: If you have a VPN connection between your on-premises network and AWS, this rule permits traffic between the VPN endpoints and your instances.
Outbound Rules:
Allow All Outbound Traffic to VPC:
- Rule: Rule number can be anything
- Protocol: All
- Port Range: All
- Destination: VPC CIDR block
- Allow/Deny: Allow
- Explanation: This rule lets instances communicate with resources within the same VPC, ensuring unrestricted internal communication.
HTTP and HTTPS Outbound:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 80 (HTTP) and 443 (HTTPS)
- Destination: Any
- Allow/Deny: Allow
- Explanation: Enable outgoing HTTP and HTTPS connections, essential for instances to access web services and APIs.
DNS Queries:
- Rule: Rule number can be anything
- Protocol: UDP
- Port Range: 53
- Destination: DNS server IP addresses
- Allow/Deny: Allow
- Explanation: This rule allows instances to send DNS queries to resolve domain names.
SMTP Email Traffic:
- Rule: Rule number can be anything
- Protocol: TCP
- Port Range: 25 (SMTP)
- Destination: Specific SMTP server IP addresses
- Allow/Deny: Allow
- Explanation: Permit instances to send outgoing email traffic to designated SMTP servers.
NTP Outbound:
- Rule: Rule number can be anything
- Protocol: UDP
- Port Range: 123
- Destination: NTP server IP addresses
- Allow/Deny: Allow
- Explanation: Allow instances to synchronize their time with NTP servers, ensuring accurate timekeeping.
Some commonly used Security Groups’ inbound and outbound rules, along with explanations of what they do:
Inbound Rules:
Allow SSH Access:
- Rule: Rule number can be anything
- Type: SSH (22)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: This rule enables secure remote access to instances via SSH. By specifying the allowed source IP range, you restrict SSH access to authorized locations.
Allow HTTP Access:
- Rule: Rule number can be anything
- Type: HTTP (80)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: This rule allows incoming HTTP traffic, essential for web servers and websites. It enables users to access your web content.
Allow HTTPS Access:
- Rule: Rule number can be anything
- Type: HTTPS (443)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: Similar to the HTTP rule, this rule permits incoming HTTPS traffic, providing secure communication for sensitive data.
Allow RDP Access:
- Rule: Rule number can be anything
- Type: RDP (3389)
- Source: Specific IP range or CIDR block
- Allow/Deny: Allow
- Explanation: This rule enables Remote Desktop Protocol access for Windows instances. It facilitates remote administration and management.
Allow Database Access from Application Servers:
- Rule: Rule number can be anything
- Type: Custom TCP Rule
- Port Range: Database port (e.g., 3306 for MySQL)
- Source: Security Group ID of application server
- Allow/Deny: Allow
- Explanation: This rule permits communication between application servers and database servers. Using Security Group IDs ensures secure and efficient data exchange.
Outbound Rules:
Allow All Outbound Traffic:
- Rule: Rule number can be anything
- Type: All traffic
- Destination: 0.0.0.0/0
- Allow/Deny: Allow
- Explanation: This rule allows instances to communicate with any external destination. While it provides flexibility, consider limiting it for security reasons.
Allow Outbound HTTP and HTTPS Traffic:
- Rule: Rule number can be anything
- Type: HTTP (80) and HTTPS (443)
- Destination: Any
- Allow/Deny: Allow
- Explanation: This rule permits instances to connect to external web servers and services over HTTP and HTTPS, supporting web-based interactions.
Allow DNS Queries:
- Rule: Rule number can be anything
- Type: DNS (53)
- Destination: DNS server IP addresses
- Allow/Deny: Allow
- Explanation: This rule enables instances to send DNS queries for domain name resolution to DNS servers.
Allow SMTP Email Traffic:
- Rule: Rule number can be anything
- Type: SMTP (25)
- Destination: Specific SMTP server IP addresses
- Allow/Deny: Allow
- Explanation: This rule facilitates instances sending outbound email traffic to designated SMTP servers.
Allow NTP Outbound:
- Rule: Rule number can be anything
- Type: NTP (123)
- Destination: NTP server IP addresses
- Allow/Deny: Allow
- Explanation: This rule lets instances synchronize their time with NTP servers, ensuring accurate timekeeping.


